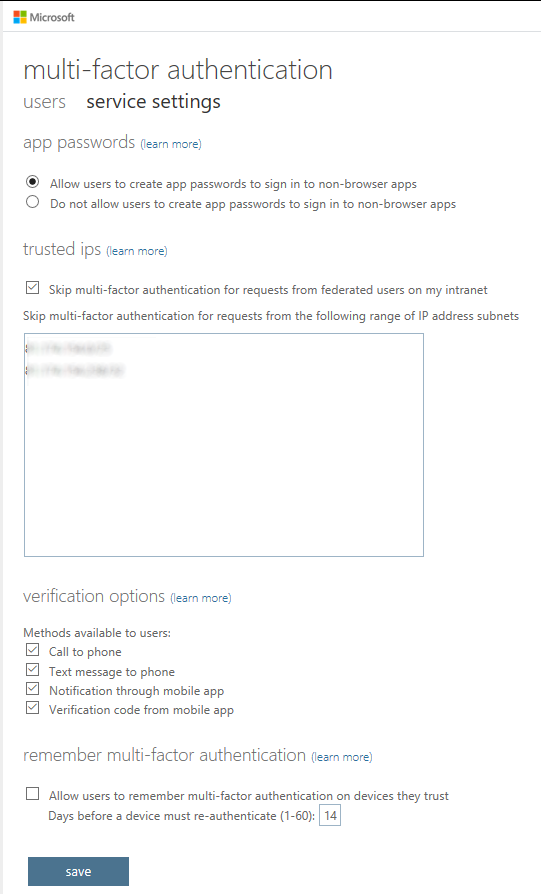
You can configure Azure/Office 365 to not require multi-factor authentication from your office
I've been working my way through the Architecting Azure Solutions (70-534): Infrastructure and Networking course on Pluralsight and discovered a useful nugget of information about the way you can configure multi-factor authentication for Office365/Azure. If you browse to https://account.activedirectory.windowsazure.com/UserManagement/MfaSettings.aspx there's a variety of settings that you can configure:
The one I'm talking about here is the text-field under "trusted ips". In here, using CIDR notation, you can describe the IP address/address range of your office network (or other trusted locations) and then users who are authenticating against Azure will not be required to go through multi-factor authentication when their requests are coming from those IP address range(s). If yours users operate mostly from office locations, it's a great way to ensure their accounts are multi-factor auth protected, but also remove some of the "friction" of having it enabled for them. If someone's working from home (but not connected to a VPN), they'll be prompted to provide a second factor, but if they're sat at their desk in office and have forgotten their mobile (if they're using a TOTP code, for example), no matter - they're not going to get prompted!