Restricting access to Azure resources with Virtual Network service endpoints & Firewall
So, there have been a couple of related announcements from the Azure peeps over the past few days:
- Azure Networking announcements for Ignite 2017
- Announcing Virtual Network integration for Azure Storage and Azure SQL
- Announcing Preview of Azure Storage Firewalls and Virtual Networks
The *very* short version, at least of the bit that particularly interests me and is the focus of this post, is that you can now restrict access (in preview so in a limited set of locations, for now) to storage accounts and other resources to specific VNets and IP addresses. Prior to this functionality existing, if you had access to a storage account, you had access to it from anywhere. This did also mean that if someone discovered credentials (e.g. Access Keys) then away they went!
To demonstrate how this works, I've created a new storage account in the East US region, and associated a new VNet with it:
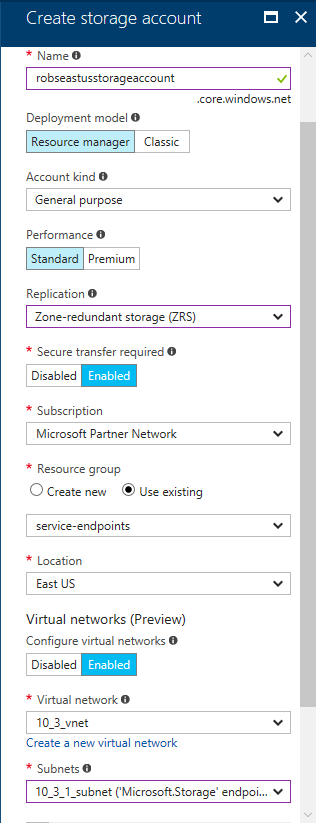
Once I'd clicked 'Create' and the account had been provisioned, the next thing to do was to verify that access to the storage account from outside the VNet had indeed been inhibited. The quickest way that I could think of to do this was to run a couple of PowerShell commands:
$storageContext = New-AzureStorageContext -StorageAccountName "robseastusstorageaccount" -StorageAccountKey "MY_STORAGE_KEY_HERE"
Get-AzureStorageContainer -Context $storageContext
The good news is, this failed! Which is exactly what I was expecting to see as my PC is not inside the 10_3_vnet virtual network:
Get-AzureStorageContainer : The remote server returned an error: (403) Forbidden. HTTP Status Code: 403 - HTTP Error Message: This request is not authorized to perform this operation using this source IP MY_IP_ADDRESS.
At line:1 char:1
+ Get-AzureStorageContainer -Context $storageContext
+ ~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~
+ CategoryInfo : CloseError: (:) [Get-AzureStorageContainer], StorageException
+ FullyQualifiedErrorId : StorageException,Microsoft.WindowsAzure.Commands.Storage.Blob.Cmdlet.GetAzureStorageContainerCommand
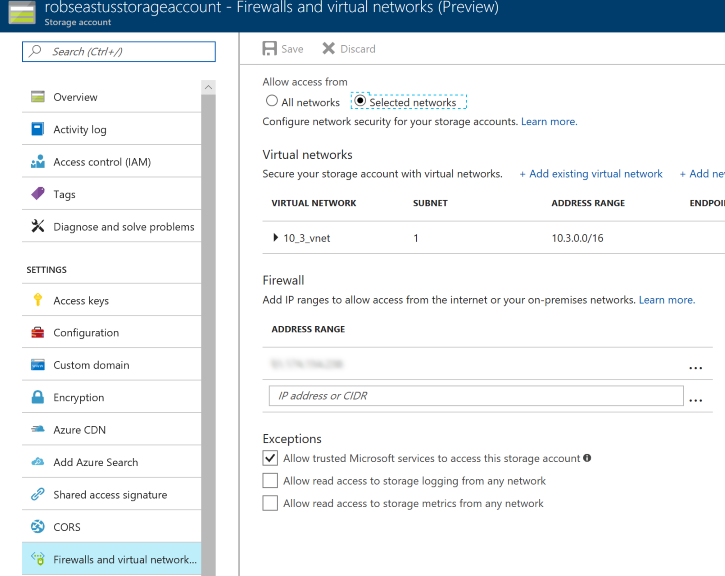
Now, as well ass being able to restrict access to a specific VNet, there's also the option to bring additional "outside world" IP addresses / ranges into the whitelist. Adding my IP address to "Firewall" under "Firewalls and virtual networks":
The result of re-running Get-AzureStorageContainer -Context $storageContext is:
CloudBlobContainer : Microsoft.WindowsAzure.Storage.Blob.CloudBlobContainer Permission : Microsoft.WindowsAzure.Storage.Blob.BlobContainerPermissions PublicAccess : Off LastModified : 29/09/2017 10:15:15 +00:00 ContinuationToken : Context : Microsoft.WindowsAzure.Commands.Common.Storage.AzureStorageContext Name : a-container
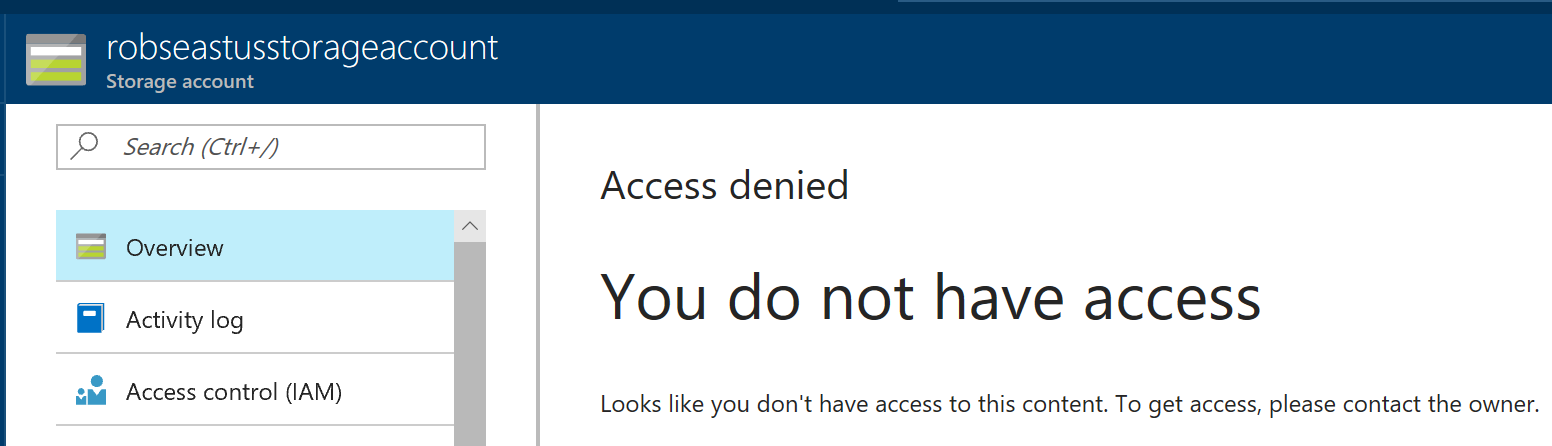
Or, in other words, enumeration of the containers in the storage account. Success! One oddity that I did notice is that before I added my local IP address to thee Firewall, I'd see "You do not have access" on the "Overview" page:
This does feel a little counter-intuitive; if I'm in the Azure portal with sufficient access to modify the list of VNet's/IP addresses that can access the storage account, I'm already stood in the doorway with the air-tight hatch open..?